Clubhouse is a drop-in voice chat platform that has taken the post-quarantine world by storm. Its simple yet alluring way of providing a space for casual conversations has netted the app over 10M downloads, but this success does not come without compromises.
This in-depth privacy analysis will demonstrate not only that Clubhouse falls below Facebook's privacy standards, but that all conversations are recorded, users are coerced into sharing their contact information, and personal data is relentlessly collected, tracked and freehandedly shared with advertising corporations.
They're listening.
Despite the significant advancements in modern cryptography over the last decade, Clubhouse does very little to protect the confidentiality of your conversations. Facebook's WhatsApp first adopted end-to-end encryption in 2014 — rendering impossible for even WhatsApp to access your conversations, with several other communication platforms following suit soon after. And seven years later, Clubhouse has failed to adopt this mainstream security measure at the expense of your privacy.
In addition to this shortcoming, their own privacy policy states that:
Solely for the purpose of supporting incident investigations, we temporarily record the audio in a room while the room is live. [...] If no incident is reported in a room, we delete the temporary audio recording when the room ends. [...]
This means that every conversation, including those that take place in private rooms, are saved to disk. While they do claim to delete these recordings once they are no longer needed, these types of claims are unverified by their very nature, and often turn out to be incorrect. Facebook previously claimed to hash all passwords before storing them, only to be fined $2.2 billion for inadvertently storing hundreds of millions of passwords in some log files.
The server infrastructure for most internet services is often quite complex, with traffic being routed through several different reverse proxies and third party services before arriving at the final destination. There is no telling whether or not any one of these endpoints accidentally stored some personal information along the way. This fact is further exemplified by the following:
To assist us in meeting business operations needs and to perform certain services and functions, we may share Personal Data with vendors and service providers, including providers of hosting services, audio applications and infrastructure, cloud services [...]
Clubhouse admits that your personal information is not only passing through their infrastructure, but many other third party applications, including the ones that handle the audio of your rooms. These third parties have no obligation to delete personal data within this privacy policy, so while Clubhouse themselves may indeed remove these recordings, you are putting your faith in the goodwill of the unnamed "vendors and service providers" to do the same.
Their policy does claim that these audio recordings are "encrypted" while conveniently failing to elaborate how. They plainly state that their recordings are listened to if at least one user in the room reports it, which requires that they own the keys for this encryption, because they need to decrypt it to listen. This is known as "server-side encryption."
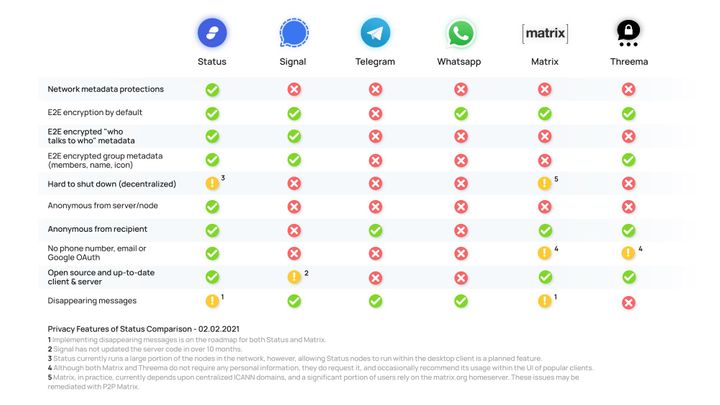
Suppose you are presented with a safe, and directly adjacent to this safe was a small piece of paper, neatly placed on a table, with the exact combination to said safe. Is this secure? This is sort of how server-side encryption works. By contrast, if you sent a message through an encrypted messenger such as Status, the keys for this end-to-end encryption never leave your device, and no one can decrypt the message except you and the intended recipient.
They're hoarding your data.
Upon joining Clubhouse, you are required to provide your phone number. While this may seem reasonable enough in this day and age, it's not so much about what they ask for, but what they do with this information. For instance, although the private messaging app, Signal, does require a phone number, it takes a number of steps to ensure that your number isn't tied to any of your activity. If you were to provide Signal with a given number, the most they could tell you is whether or not this number is a Signal user.
And what Clubhouse does is a lot:
- They sell your data to "social media platforms and other advertising partners that will use that information to serve you targeted advertisements."
- They indefinitely store all data they collect according to their retention policy, and they do not provide any in-app way of deleting your account.
- They use invisible tracking images called pixels in your emails "that allow [them] to collect your email and IP address as well as the date and time you open an email or click on any links in the email."
- They claim to "make reasonable commercial efforts to recognize and support 'Do Not Track' signals" despite the fact that it is impossible to enable this signal within the app, where the overwhelming majority of the tracking occurs.
Notwithstanding the extensive data sharing Clubhouse engages in, they also employ coercive measures to acquire this data. When you attempt invite another user to Clubhouse, you will be required to give up your entire contact list – which will be indefinitely stored on their servers and shared with their advertising partners. No contacts, no inviting. This may actually be in violation of Apple's policies on protecting user privacy.
The App Store requires that all apps that ask for certain permissions to fail gracefully if they are declined. This simply means that if your scientific calculator app asks for your precise location, and you decline, everything should still work because the calculator evidently doesn't need your location. The only times where apps can block the user from doing certain things is if the permission in question is required for the core functionality, such as a camera app asking for permission to use your camera.
In Clubhouse's case, there appears to be no legitimate reason for them to need all of your contacts simply to be able to invite another user. If you join Clubhouse to speak with a friend of yours, the only data needed is the contact information of that specific friend. These requirements are subtle yet pernicious methods to amass as much personal information as possible.
The immediate defense one may present is that this contact information is used to build a social graph and to aid user discovery. While this is, in part, truthful, it escapes the fact that providing such social discovery without ever collecting or seeing any personal information has been possible for nearly four years. Signal first announced its private contact discovery in 2017, which allows users to easily connect with their friends and family without ever revealing their contact list to the Signal service. This methodology has only become simpler and more accessible since.
Defend yourself.
As we approache a digital-first world at warp speed, it is crucial to recognize the importance of one's privacy, and the ever-increasing rate at which it is decaying. In part due to the rise in popularity of cryptocurrencies, the field of cryptography has never advanced at a faster rate, with truly novel and innovative projects such as Nym, Aztec Networkand Zcash holding on to what might be our last chance at a private internet. Defend yourself with cryptography.