Smart Appliance Spying
We are so often concerned with—and building for the purposes of—online privacy, that we have been less focused on a different type of privacy invasion. Privacy in your own home is under attack.
Check out how we protect the right to private & secure conversations

We are so often concerned with—and building for the purposes of—online privacy, that we have been less focused on a different type of privacy invasion. Privacy in your own home is under attack.
Man is a political creature and one whose nature is to live with others. - Aristotle Persons do not exist as such without a world

the internet, where everybody has a chance of being heard, a more democratic system — Aaron Swartz, co-founder of Reddit Reddit is a social media platform,

Facebook has better privacy standards. Clubhouse records all your conversations and shares every bit of your data with advertising corporations.
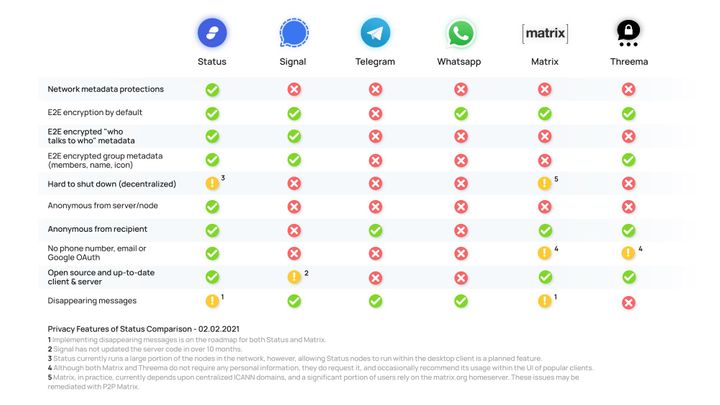
Which messenger is truly the most private? We take a look at Signal, Telegram, Status and more.

A Security Audit Checklist. Selecting the right vendor, preparing documentation, aligning on scope, creating open lines of communication, & more.

"A policeman's job is only easy in a police state." - Orson Welles

The recent Coinbase Card is said to "eliminate the middleman" – but does it really?
With the v1.8 release, Status aims to improve your control over your communication and your finances.
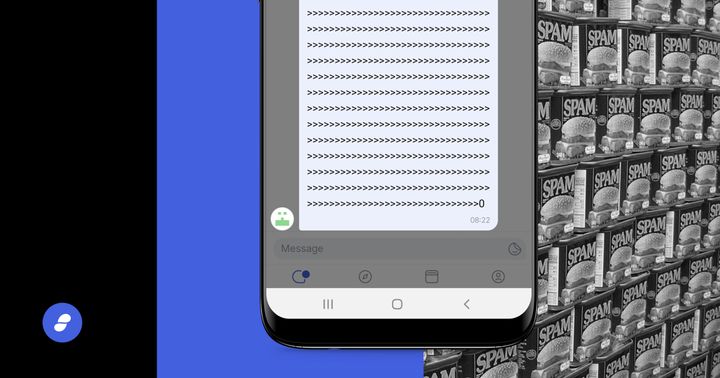
This deep-dive article explores the historical context of spam, reviews mitigations on relevant platforms, challenges in the context of Status principles and architecture, current countermeasures and future proposals with their pros and cons.
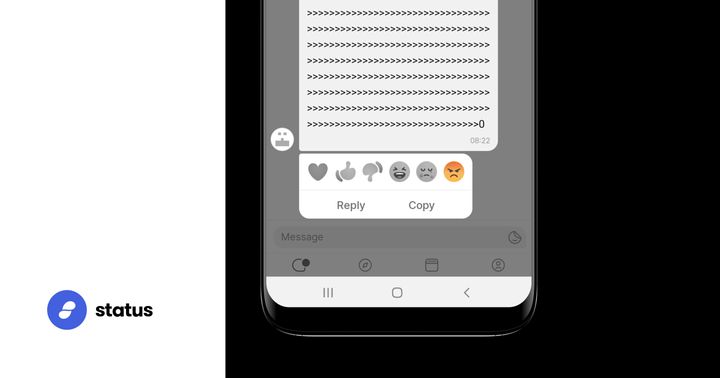
Mitigation efforts are in place with mid-term and long term solutions being explored for a spam attack that has happened in some Status public channels. Learn more about the efforts

One of the principal sources of the omnipresent data collection and surveillance we see today lies in the inherently secretive and centralized development of most applications. Status delivers security and trust through open source software

Privacy is the power to selectively reveal oneself to the world. Three types of identities make this possible - Real, pseudonymous, and completely anonymous. Status is a pseudonymous platform

We reflect on the topic of ‘privacy versus convenience’ and how they often seem to conflict with each other. We explore this in the context of account identifiers on Status messenger and evaluate this choice in light of the recent debate around PIN-related features of the Signal messenger.

Pseudo-anonymity enables an open society. Pseudo anonymity enables the right to privacy for one’s real self while enabling the “right to access” and reputations as social currency.